Cambium Data Blog
In business, it’s often the case that you spend more time talking about work than you spend actually doing the work. How many emails have you sent recently that could be described as “email tennis?” We won’t mince words; this endless back-and-forth discussing meeting times, checking calendars, and re-typing the same responses day-in and day-out is increasing your administrative friction and wasting your time.
Today, we’re exploring three ways you can automate scheduling and communication to put an end to the emails and finally get back to work.
Email is a vital tool to have in the workplace, but it still deals with its fair share of issues—particularly in regards to time wasters and security risks. You can save time, money, and future headaches by proactively addressing your email policies. Today, we want to look at two ways you can keep email from holding your business back: spam blocking and archival solutions.
Chances are you get a lot of unwanted messages, whether it’s spam or messages from threads, feeds, or newsletters you no longer want to receive. Thanks to some nifty built-in features in Gmail and Microsoft Outlook, you can easily unsubscribe from pretty much any website that’s sending you boatloads of emails, and it’s as easy as clicking a link.
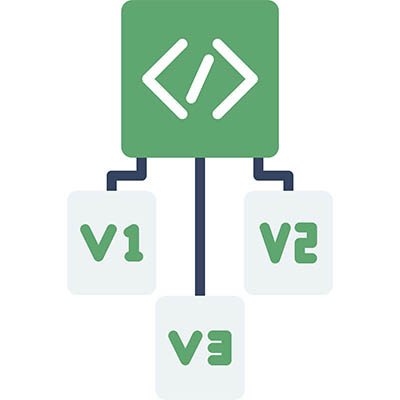
How many times have you accidentally made changes to a file, only to wish that you didn’t? Maybe you accidentally overwrote an important document, or someone made unapproved edits to an important company document. In all of these cases, version control—being able to see the different iterations of a file—is critically important. Here’s why you need a solution in place that offers version control.
Most, if not all, of us have heard the most famous phishing story of them all: how the ancient city of Troy, after ten years of war, finally fell after a raiding party was allowed into the gates by hiding in the belly of a constructed wooden horse. It’s true… the legend of the Trojan horse, already associated by name with a nasty cyberattack, is arguably also a cautionary tale about how effective phishing can be.
Let’s go over how you can help protect your business from falling for this truly classic ruse.
Good communication is key for any business. Today, there are tons of ways companies stay connected: phone calls, emails, messaging apps, and video meetings. While all these tools can be helpful, they can also get confusing if not managed properly. Let’s break down the basics of business communication so it’s easy to understand.
When you check how much your company spends on communication tools, you might not be happy with the numbers. If you feel like you're paying too much for too little, you're not alone. Many businesses are switching to modern communication tools that use the Internet. Let’s explore some of these options.
We’re always telling people to avoid clicking on suspicious links, but the bad guys are making it harder to tell the difference between a legitimate URL and a suspicious one. We’re going to try to simplify it for you, and have you focus on the placement of a single punctuation mark in a link to tell if it might be safe or dangerous.
In business, email is one of the tried and true methods of communication. Unfortunately, there are many out there searching to breach a network, whether it be to deploy malware or lie in wait until they have access and cause havoc from within. Regardless of what strategy hackers and scammers use, it is important that users understand what to do to protect themselves and their organizations’ email. Here are some tips to keep in mind.
Printing has been a major part of most businesses for a long time. It’s how ideas were shared for decades. The past couple, however, have seen the need for printed resources go way down, but that often doesn’t stop businesses from wasting useful capital on unnecessary printing. This month, we thought we’d give you three tips to help you reduce your printing costs, month after month.
It’s easy to think of email as something that just works. You open up Outlook or log into Gmail and your mail is there. Most people aren’t even aware of the vast, complex set of systems required for email to even work—and we don’t blame you. It’s extremely complicated.
That being said, if nobody is actively managing your email, providing protection for the underlying technology, and making sure that it was and remains configured properly, it’s possible that your email could be working fine while opening you up for unseen threats.
Have you tried using Enhanced Safe Browsing in your Google Chrome browser? This feature has been a part of the browser since 2019, and it was implemented with the intention of preventing phishing attacks. This feature was also recently added to Gmail. Here’s how you enable it, as well as why it might not be the solution you’re hoping for.